You are being diligent with your cybersecurity training, you are not opening suspicious e-mails, and then it happens...
... You get a regular, old message from a colleague inviting you join a group or open an important file through your SharePoint access.
Office 365 users and admins should be on the lookout for a phishing email that has spoofed sender addresses as this is part of a new phishing attack.
It has all the right Microsoft logos and terminology on it in all the right places.

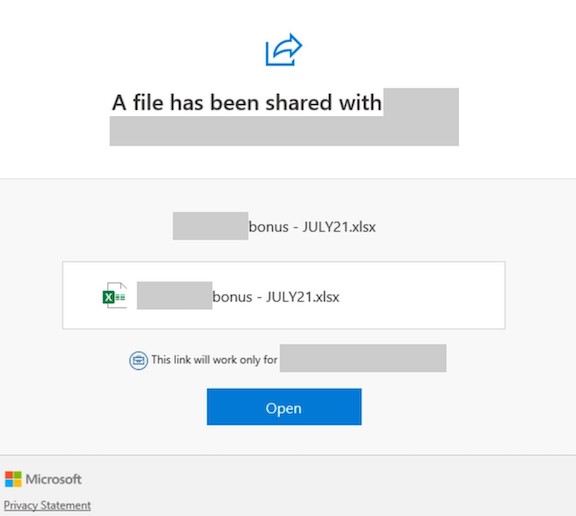
Microsoft’s Security Intelligence team issued an alert after noticing the fact that an active campaign is targeting Office 365 organizations.
The M.O. used relies on convincing emails and a few other techniques that are used to bypass phishing detection, that include an Office 365 phishing page, a Google cloud web app hosting, and also a compromised SharePoint site that pushes victims to insert their credentials.
An active phishing campaign is using a crafty combination of legitimate-looking original sender email addresses, spoofed display sender addresses that contain the target usernames and domains, and display names that mimic legitimate services to try and slip through email filters.
The original sender addresses contain variations of the word “referral” and use various top-level domains, including the domain com[.]com, popularly used by phishing campaigns for spoofing and typo-squatting.
It’s concerning to see that phishing remains a tricky issue that businesses are still facing; therefore the existence of phishing awareness pieces of training is highly recommended both by CISA and Microsoft.
Phishing is an important component of business email compromise (BEC) attacks, as it helps the attacker to hack into a corporate e-mail account and impersonate the owner of the account with ease.
BEC attacks cost Americans over $4.2 billion last year, according to the latest figures released by the FBI, in this way being more expensive than ransomware attacks.
When looking at the main phishing URL, the researchers noticed that it relies on a Google storage resource that sends the victim to the Google App Engine domain AppSpot.
The emails contain two URLs that have malformed HTTP headers. The primary phishing URL is a Google storage resource that points to an AppSpot domain that requires the user to sign in before finally serving another Google User Content domain with an Office 365 phishing page.
A second URL is embedded in the notifications settings and sends the victim to a compromised SharePoint site. It’s interesting to note that both URLs require sign-in to get to the final page, therefore allowing the attack to bypass sandboxes, and making this campaign to be considered “sneakier than usual” according to Microsoft.
Beware, and share with your staff. As always, River Run can help.
Topics
Share this article